To create a webhook go to your Pentest-Tools.com dashboard and find the integrations menu on the sidebar. Here you can configure integrations with 3rd-party apps which you can later use for notifications (Slack, Webhooks), or vulnerability management workflows (JIRA). More integrations will be added in the future.
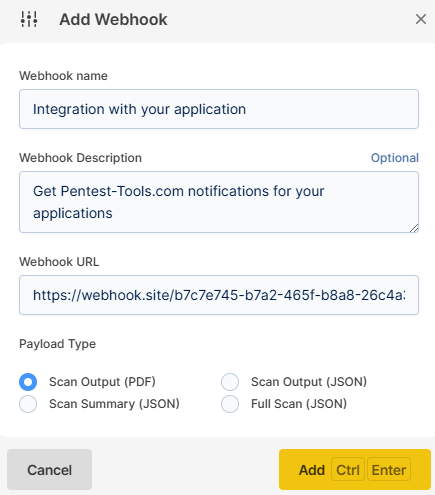
When you enter the webhook configuration, click + Add New and a window will open containing 4 categories:
- Webhook name - here you will fill in the name of the webhook you will create
- Webhook description - here you will fill in a description that will help you understand in the future what that webhook does
- Webhook URL - here you will fill in the URL to which the webhook will send the data to
- Webhook Payload Type - here you will choose what kind of data to be sent to the Webhook URL
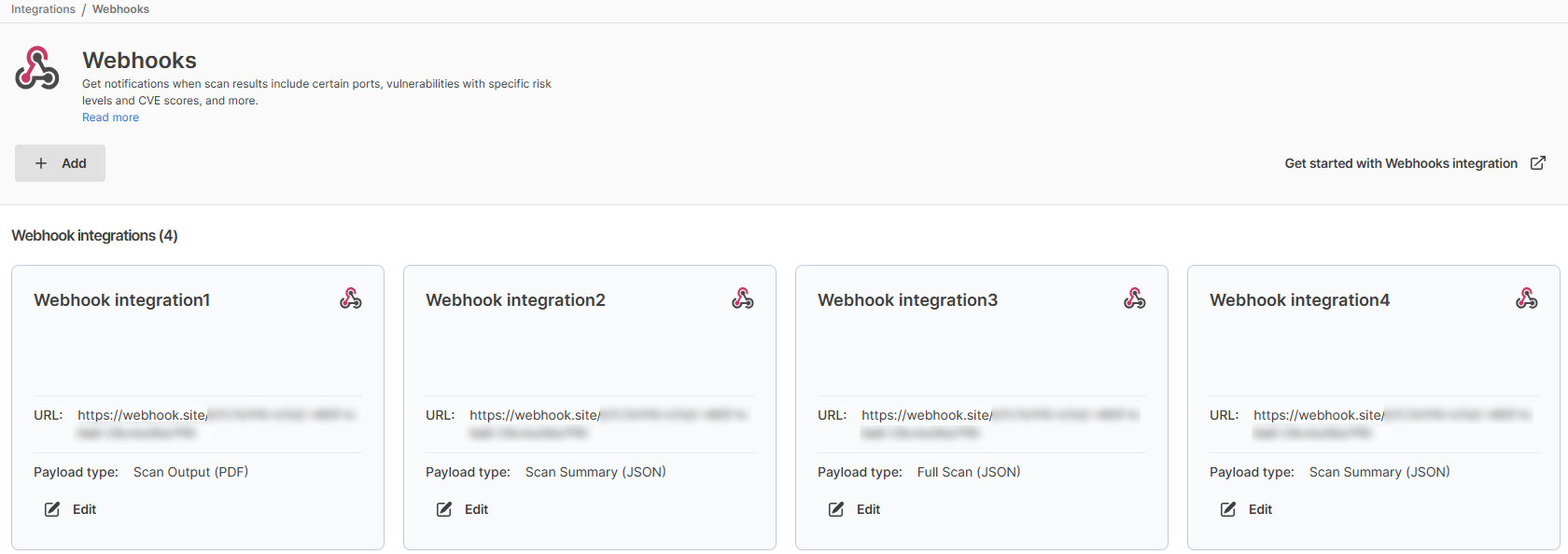
There are 4 kinds of data (Webhook Payload Type) that you can send:
- Scan Output (PDF)
- Scan Output (JSON)
- Scan Summary (JSON)
- Full Scan (JSON)
Each one of these 4 options allows you to send a type of payload to the specified URL whenever a selected event occurs.
Also, multiple webhooks can be created from this page so you can send data to multiple endpoints.
After adding a new webhook, you can use it by configuring a new Notification and enabling the webhook action. Here are some examples of how the webhook payload type will look, for each of the 3 options:
1. The PDF output is a standard scan result, see here a sample report.
2. Scan output JSON - see an extract below
{
"id": 210909598,
"type": "vulnerability",
"status": 0,
"source": 0,
"task_id": 32577432,
"target_id": 37151048,
"name": "Cross-Site Scripting",
"test_id": 40,
"test_description": "Checking for Cross-Site Scripting...",
"test_finished": true,
"vuln_evidence": {
"type": "table",
"data": [
[
"<b>URL</b>",
"<b>Method</b>",
"<b>Vulnerable Parameter</b>",
"<b>Evidence</b>",
"<b>Replay Attack</b>"
],
[
"<a href='https://pentest-ground.com:4280/vulnerabilities/xss_r/' target='_blank' rel='external noopener noreferrer nofollow'>https://pentest-ground.com:4280/vulnerabilities/xss_r/</a>",
"GET",
"name\n(Query Parameter)",
"Injected the payload <code><sVg/onLOad=document.body.append(`b8a2de4e`.repeat(2))></code> in the <strong class=text-semibold>name query parameter</strong> and the expected result <code>b8a2de4eb8a2de4e</code> was found in the response.\nThe script inside the payload tries to repeat a random string. If the string <code>b8a2de4e</code> is doubled on the response page, we confirm that our script has been executed.\nThis request was done using a Chrome browser.\n\nIf available, the replay attack button uses a simpler <code>alert()</code> payload that may not work as expected.\nTo validate the vulnerability, we attempted to extract some data exposed by the application in the browser.\nThe application uses the following (non-HttpOnly) cookies: <strong class=text-semibold><ul><li>SessionID:encrypted-session-id</li><li>security:low</li><li>env:graphiql:disable</li><li>_ga:GA1.1.1896500464.1732279488</li><li>PHPSESSID:015c8a6e02192c04b814ce3795171341</li><li>_ga_Z3XCDXSJ3P:GS1.1.1732279487.1.1.1732279556.60.0.0</li><li>_gcl_au:1.1.1454887252.1732279487</li></ul></strong>\n<a style=\"font-size:12px\" href='https://ptt.eu-central-1.linodeobjects.com/ptt/6ed2af09527a7a9e.txt' target='_blank' rel='external noopener noreferrer nofollow'>Request / Response</a>",
"<a href='https://pentest-ground.com:4280/vulnerabilities/xss_r/?name=1d3d2d231d2dd4%3CsVg%2FonLOad%3Dalert%28document.domain%29%3E#pttedc4b706=' target='_blank' rel='external noopener noreferrer nofollow' title='Attack Target'><i class='fa fa-rocket btn-attack'></i></a>"
]
]
},
"how_to_reproduce": null,
"vuln_description": "We found that the target web application is vulnerable to Cross-Site Scripting (XSS) attacks. This vulnerability is caused by inadequate input validation, allowing a malicious actor to inject and execute JavaScript code in the context of another user's session.",
"vuln_risk_description": "The risk is that the code injected by an attacker could potentially lead to effects such as stealing session cookies, calling application features on behalf of another user, exploiting browser vulnerabilities.\nSuccessful exploitation of Cross-Site Scripting attacks requires human interaction (e.g. determine the user to access a special link by social engineering).",
"vuln_risk_level": {
"name": "HIGH",
"value": 3,
"label": "High",
"color": "red"
},
"vuln_recommendation": "There are several ways to mitigate XSS attacks. We recommend to:\n- never trust user input\n- always encode and escape user input (using a Security Encoding Library)\n- use the HTTPOnly cookie flag to protect from cookie theft\n- implement Content Security Policy\n- use the X-XSS-Protection Response Header.",
"vuln_references": [
"https://owasp.org/www-community/attacks/xss",
"https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html"
],
"cvss_v2": -1,
"cvss_v3": -1,
"vuln_cve": "",
"vuln_cwe": "CWE-79",
"vuln_owasp2017": "A7 - Cross-Site Scripting (XSS)",
"vuln_owasp2021": "A3 - Injection",
"confirmed": true,
"discovery_data": null,
"creation_date": null,
"is_verified": true,
"original_risk_level": {
"name": "HIGH",
"value": 3,
"label": "High",
"color": "red"
},
"is_cloned": false,
"vuln_id": "WEBSCAN-00-0000012",
"screenshots": null,
"port": null,
"protocol": null,
"service": null,
"group_id": 27978559,
"cve": "",
"cvss": -1,
"cwe": "CWE-79",
"owasp2017": "A7 - Cross-Site Scripting (XSS)",
"owasp2021": "A3 - Injection",
"risk_description": "The risk is that the code injected by an attacker could potentially lead to effects such as stealing session cookies, calling application features on behalf of another user, exploiting browser vulnerabilities.\nSuccessful exploitation of Cross-Site Scripting attacks requires human interaction (e.g. determine the user to access a special link by social engineering).",
"risk_level": 3,
"recommendation": "There are several ways to mitigate XSS attacks. We recommend to:\n- never trust user input\n- always encode and escape user input (using a Security Encoding Library)\n- use the HTTPOnly cookie flag to protect from cookie theft\n- implement Content Security Policy\n- use the X-XSS-Protection Response Header."
},3. Scan summary JSON
{
"id": 32533579,
"target_id": 37151048,
"tool_id": 170,
"status_name": "finished",
"vpn_scan": false,
"progress": 100,
"result_summary": {
"high": 0,
"medium": 0,
"low": 5,
"info": 14,
"text": ""
},
"start_time": "2024-11-20 15:24:09",
"end_time": "2024-11-20 15:24:47",
"duration": 38,
"num_tests": 19,
"num_finished_tests": 19
}4. Full Scan (JSON)
[
{
"info": {
"id": 32576674,
"target_id": 37151048,
"tool_id": 170,
"status_name": "finished",
"vpn_scan": false,
"progress": 100,
"result_summary": {
"high": 2,
"medium": 3,
"low": 10,
"info": 58,
"text": ""
},
"start_time": "2024-11-22 13:31:12",
"end_time": "2024-11-22 14:22:02",
"duration": 3050,
"num_tests": 73,
"num_finished_tests": 73
{
"id": 210901864,
"name": "Password Submitted in URL",
"test_description": "Checking for passwords submitted in URLs...",
"test_finished": true,
"confirmed": true,
"cve": [],
"cvss": null,
"vuln_description": "We found a form which is submitted using a GET method and has inputs of the type password. The end result is that passwords are submitted in URLs.",
"vuln_evidence": {
"type": "table",
"data": {
"headers": [
"URL",
"Method",
"Parameters",
"Evidence"
],
"rows": [
[
"https://pentest-ground.com:4280/vulnerabilities/brute/",
"GET",
"Headers: User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Cookies: ADMINCONSOLESESSION=QS9TpGobASKIOFMabVXHusCNxDEGJmSX2H-6PriYMPQ_kht6soXe!-1512387900 PHPSESSID=1838bdff310df04dac7c5dfbf76dbc39 SessionID=encr...",
"The following form sends inputs of type password plainly in the URL: <form action="#" method="GET"> Username: <br/> <input name="username" type="text"/> <br/> Password: <br/> <input autocomplete="off" name="password" type="password"/> <br/> <br/> <input name="Login" type="submit" value="Login"/> </form> Request / Response"
],
[
"https://pentest-ground.com:4280/vulnerabilities/csrf/",
"GET",
"Headers: User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Cookies: ADMINCONSOLESESSION=QS9TpGobASKIOFMabVXHusCNxDEGJmSX2H-6PriYMPQ_kht6soXe!-1512387900 PHPSESSID=1838bdff310df04dac7c5dfbf76dbc39 SessionID=encr...",
"The following form sends inputs of type password plainly in the URL: <form action="#" method="GET"> New password: <br/> <input autocomplete="off" name="password_new" type="password"/> <br/> Confirm new password: <br/> <input autocomplete="off" name="password_conf" type="password"/> <br/> <br/> <input name="Change" type="submit" value="Change"/> </form> Request / Response"
],
[
"https://pentest-ground.com:4280/vulnerabilities/csrf/",
"GET",
"Query: Change=Change password_conf=Secure123456$ password_new=Secure123456$ Headers: User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Cookies: ADMINCONSOLESESSION=GQFTsKSD52bNlC2DXUfTvDzyvnOhPe6G4KS0NE5...",
"The following form sends inputs of type password plainly in the URL: <form action="#" method="GET"> New password: <br/> <input autocomplete="off" name="password_new" type="password"/> <br/> Confirm new password: <br/> <input autocomplete="off" name="password_conf" type="password"/> <br/> <br/> <input name="Change" type="submit" value="Change"/> </form> Request / Response"
]
]
}
},
"risk_description": "Passwords submitted in URLs have a higher chance of being leaked. The main reason is that URLs can be leaked in browser cross-site requests via the Referer header. Additionally, URLs are usually stored in all kinds of logs. If any access or error logs of the server were publicly accessible, an attacker could also harvest password from it.",
"risk_level": 1,
"status": "open",
"recommendation": "You should submit passwords using POST rather than GET. This way sensitive data won't be shared to other locations via URLs.",
"verified": true,
"vuln_id": "WEBSCAN-00-0000033",
"owasp": {
"owasp_2017": null,
"owasp_2021": "A4 - Insecure Design"
},
"cwe": null,
"port": null,
"protocol": null,
"service": null
},
{
"id": 210901865,
"name": "File Upload",
"test_description": "Checking for file upload...",
"test_finished": true,
"confirmed": true,
"cve": [],
"cvss": null,
"vuln_description": "We found the file upload functionality in the web application. While this is not a security issue by itself, it may represent a first step in an attack involving storing data on the target server.",
"vuln_evidence": {
"type": "table",
"data": {
"headers": [
"URL",
"Method",
"Parameters",
"Evidence"
],
"rows": [
[
"https://pentest-ground.com:4280/vulnerabilities/upload/",
"GET",
"Headers: User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Cookies: ADMINCONSOLESESSION=QS9TpGobASKIOFMabVXHusCNxDEGJmSX2H-6PriYMPQ_kht6soXe!-1512387900 PHPSESSID=1838bdff310df04dac7c5dfbf76dbc39 SessionID=encr...",
"The following form allows file upload: <form action="#" enctype="multipart/form-data" method="POST"> <input name="MAX_FILE_SIZE" type="hidden" value="100000"/> Choose an image to upload: <br/> <br/> <input name="uploaded" type="file"/> <br/> <br/> <input name="Upload" type="submit" value="Upload"/> </form> Request / Response"
],
[
"https://pentest-ground.com:4280/vulnerabilities/upload/",
"POST",
"Body: MAX_FILE_SIZE=100000 Upload=Upload uploaded=This is a file Headers: Content-Type=multipart/form-data User-Agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36 Cookies: ADMINCONSOLESESSION=GQFTsKSD52bNlC2DX...",
"The following form allows file upload: <form action="#" enctype="multipart/form-data" method="POST"> <input name="MAX_FILE_SIZE" type="hidden" value="100000"/> Choose an image to upload: <br/> <br/> <input name="uploaded" type="file"/> <br/> <br/> <input name="Upload" type="submit" value="Upload"/> </form> Request / Response"
]
]
}
},
"risk_description": "The risk is that an attacker might use the file upload functionality for path traversal, persistent XSS, transmission of malware or denial of service, if such vulnerabilities are present.",
"risk_level": 0,
"status": "open",
"recommendation": "Use a server-generated filename, inspect the content of uploaded files, enforce a whitelist of non-executable file types and a size limit, and reject attempts to upload archive formats such as ZIP.",
"verified": true,
"vuln_id": "WEBSCAN-00-0000087",
"owasp": {
"owasp_2017": null,
"owasp_2021": null
},
"cwe": "CWE-434",
"port": null,
"protocol": null,
"service": null
},
},
},
],