Basic ❌ / Advanced ✔️ / Teams ✔️
How does it work?
Simply said, we create a secure tunnel between our scanning machines and your network. This way, our scanners can reach the hosts from your internal network through the VPN tunnel. For this, you need to first create a VPN Profile.
Is this secure for my network?
You should know that every packet reaching or leaving your network is fully encrypted and there is nobody else accessing your network through this channel.
Furthermore, you can configure your VPN server to allow access only to certain internal hosts that you want to scan and not to the whole network. This way you can be fully assured that nobody is messing with your network over VPN.
How to configure a scan through VPN?
Go to Settings > VPN Profiles
Click
- Docker
- Virtual Machine VPN Agent - is available in 3 popular formats: VMWare, Microsoft Hyper-V, and Oracle VirtualBox.
- AWS agent
- Custom Open VPN Server - by importing your own .ovpn configuration file into the platform
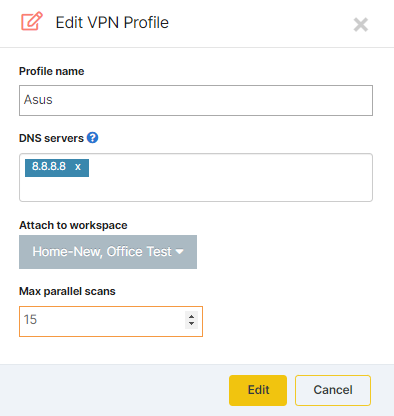
The settings will differ, depending on the option you selected above. Some key aspects are: configuring the DNS server (if applicable), attaching the profile to one or more workspaces, and adjusting the maximum number of concurrent scans to run through the VPN tunnel.
All of these can be modified at any time by editing the VPN profile.
After configuring the above-mentioned and making sure that the deployed agent/server is connected, you should also test if the connection is successful from the Pentest-Tools.com dashboard.