SSH-based authentication
Secure Shell, or simply SSH is a secure way to access a computer over a network. By default, an SSH server listens on port 22.
If the provided credentials are correct, and the port accepts the connection, this method will create a legitimate SSH session on the target. Unlike an unauthenticated Sniper scan, instead of extracting the artefacts after a successful exploit, they are extracted through the SSH session.
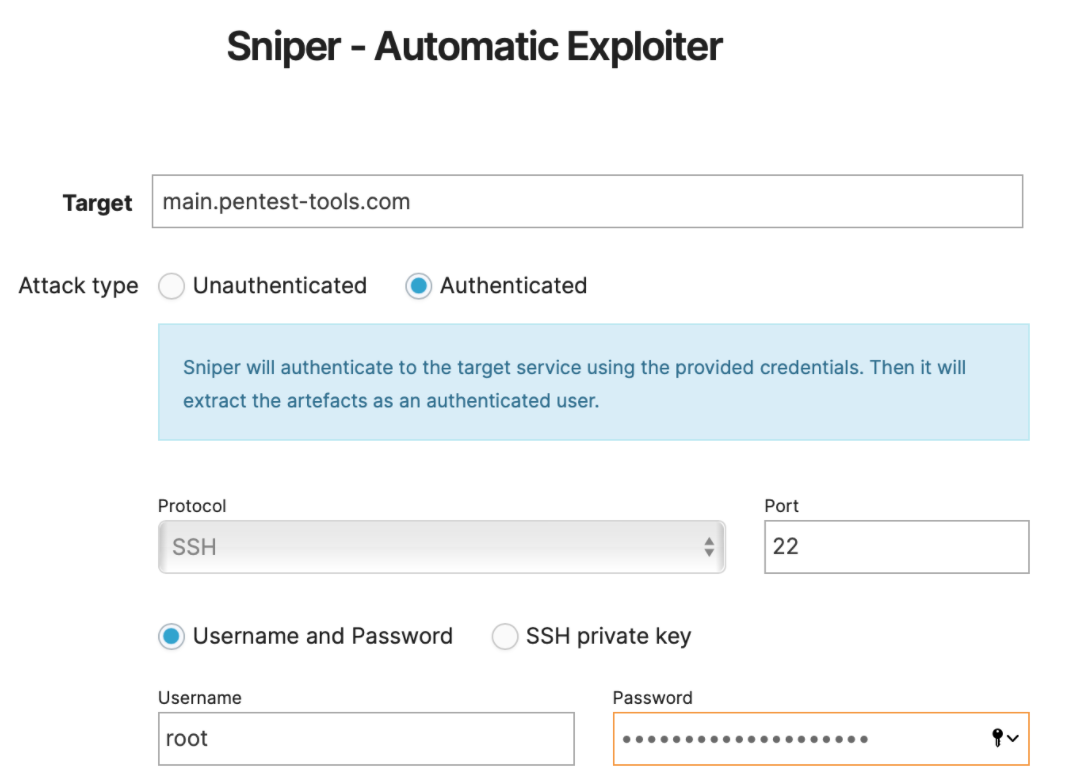
When selecting the Username and Password option, make sure to input the correct credentials, otherwise, you will receive the following error:
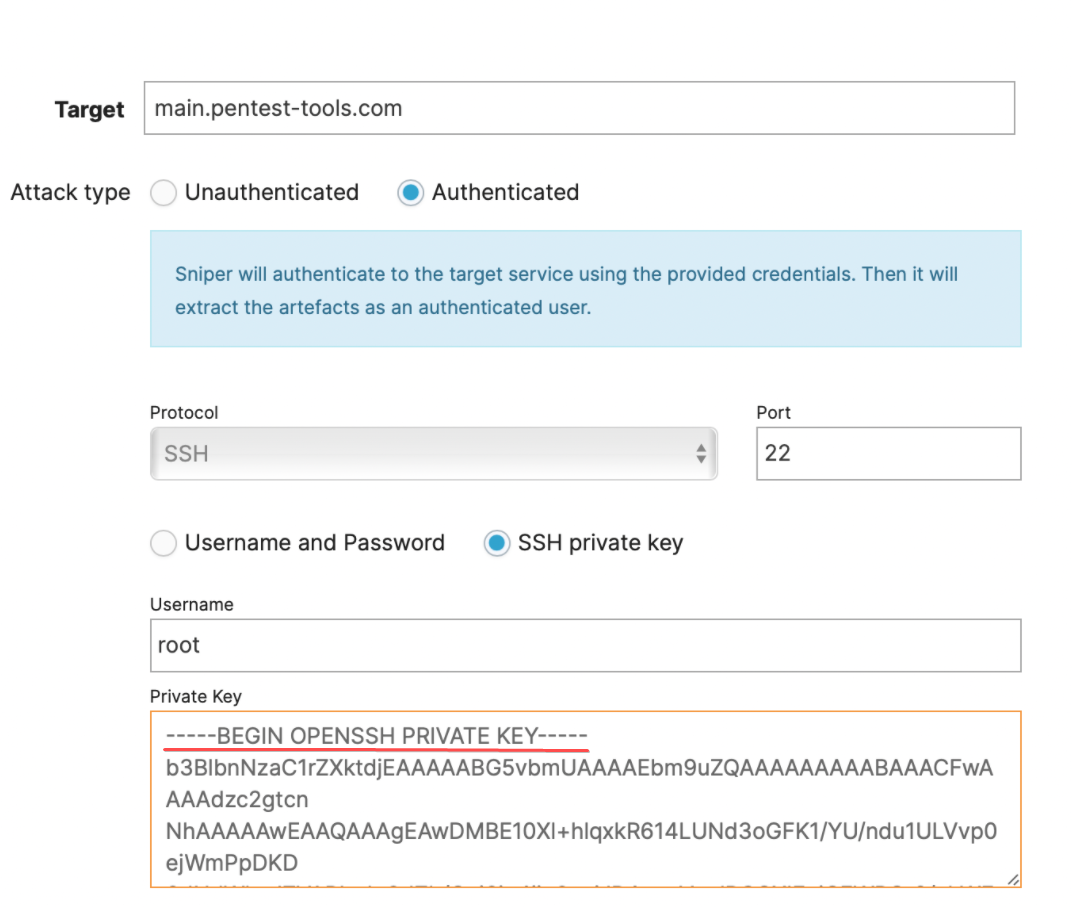
When selecting the SSH private key authentication method, input the private SSH key for the system you'd like to scan and make sure to paste the entire key, including the header & footer.
 Possible errors:
Possible errors:
This can appear if either the input port is closed, or if there is no SSH service running on that port. Make sure to check that you have inputted the correct port or if there may be any firewall that is blocking the connection.