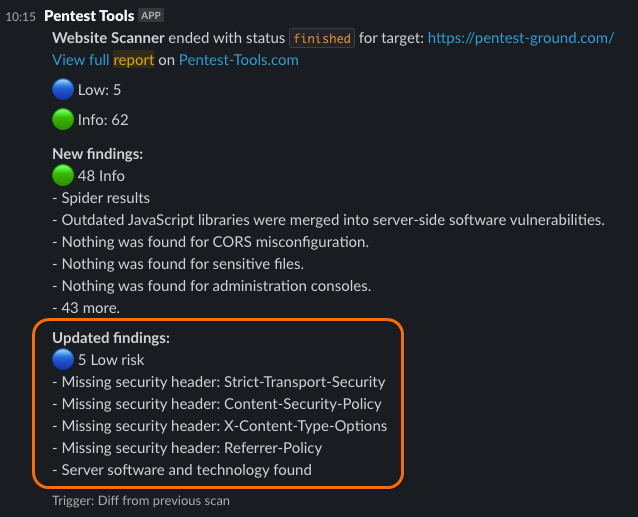
Our users often asked us how to easily view trends and changes in vulnerabilities for monitored targets.
We’re excited to announce that this feature is now fully implemented, allowing you to effortlessly track these changes. Get notified only for new findings that appear in your scans, without any workarounds.
How does it work?
After setting up a scan diff notification, we will monitor the following:
- The target you scanned,
- The workspace where the scan was initiated,
- The tool utilized,
- And the successful completion of the scan.
How to configure the scan diff notification
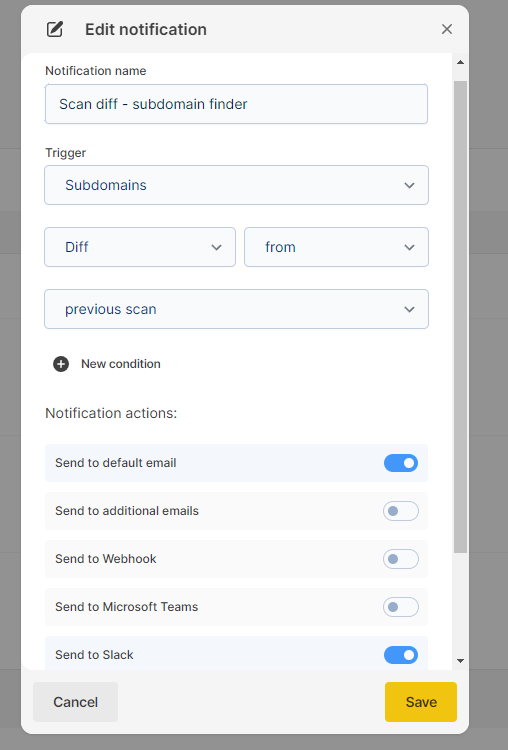
Navigate to the Settings section from the left-side menu and choose Notifications
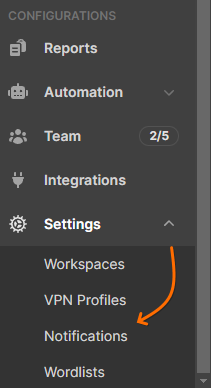
Click the +Add button to open the configuration panel and set the conditions that will trigger the notification
The scan diff triggers include the following:
- For Vulnerability Scanners
Vulnerability → Diff → from → previous scan
- For Port Scanner
Port Scanner → Diff → from → previous scan
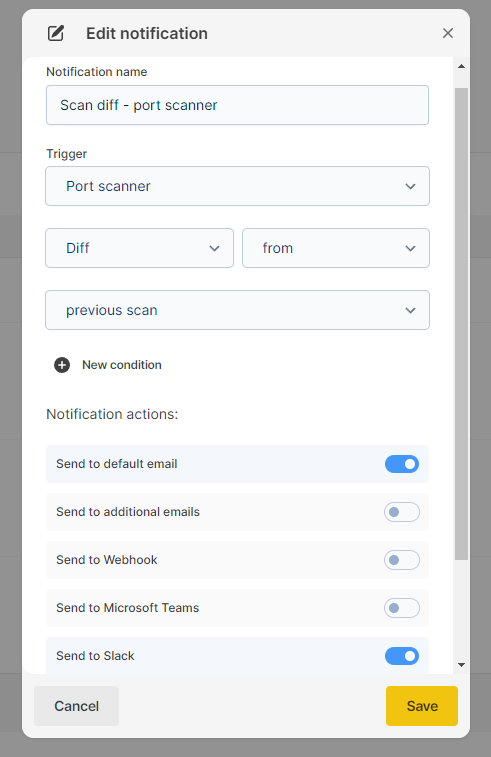
- For Subdomain Finder
Subdomains → Diff → from → previous scan
You're all set. Enjoy a quieter inbox!
After the subsequent scans are completed, you will only receive notifications if there are changes detected to the findings associated with a particular target.
As a result, you will receive notifications that either:
- Include newly detected findings, ports, or subdomains,
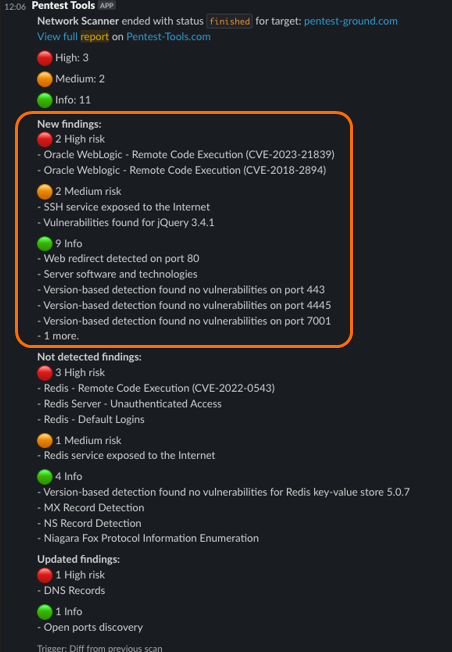
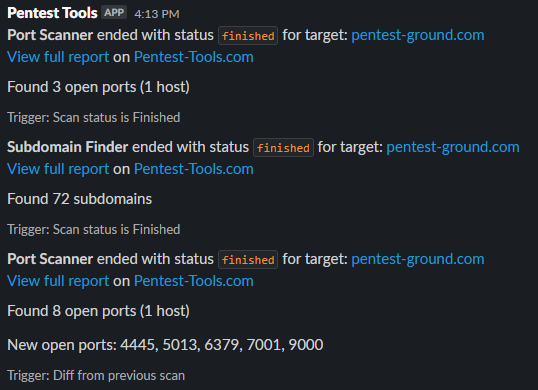
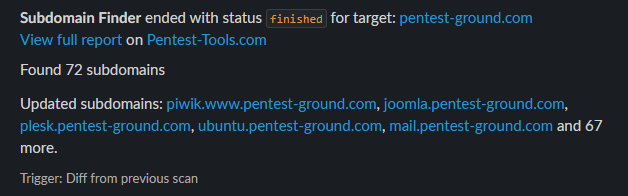
- Indicate findings that were not detected in the subsequent scans,
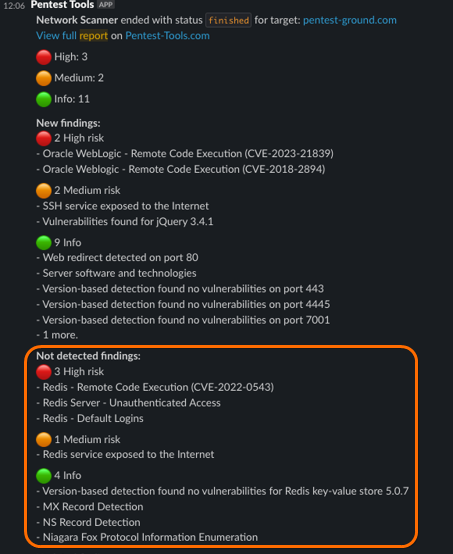
- Provide updated findings with additional information or evidence